IIoT Cyber Security Trust Center
GE Digital's industrial applications are developed with a secure-by-design mindset, and supported by cloud operations that adhere to the strictest industrial standards and latest best practices.
From the edge to the cloud
Asset Performance Management (APM), Manufacturing Data Cloud (MDC), Manufacturing, and Automation applications are built to meet the most stringent security and compliance requirements, so you can adopt the right technologies and processes that deliver positive outcomes for IIoT investments.
New, more advanced threats are targeting operational environments, so with our platform and industrial applications, you can bridge the worlds of IT and OT and protect data as it travels from the edge to the enterprise and back again. By building security into the design of our portfolio of industrial applications, we’ve assured that you can connect with confidence, knowing that your data, processes, and outcomes are delivered in a resilient environment.
Secure by design
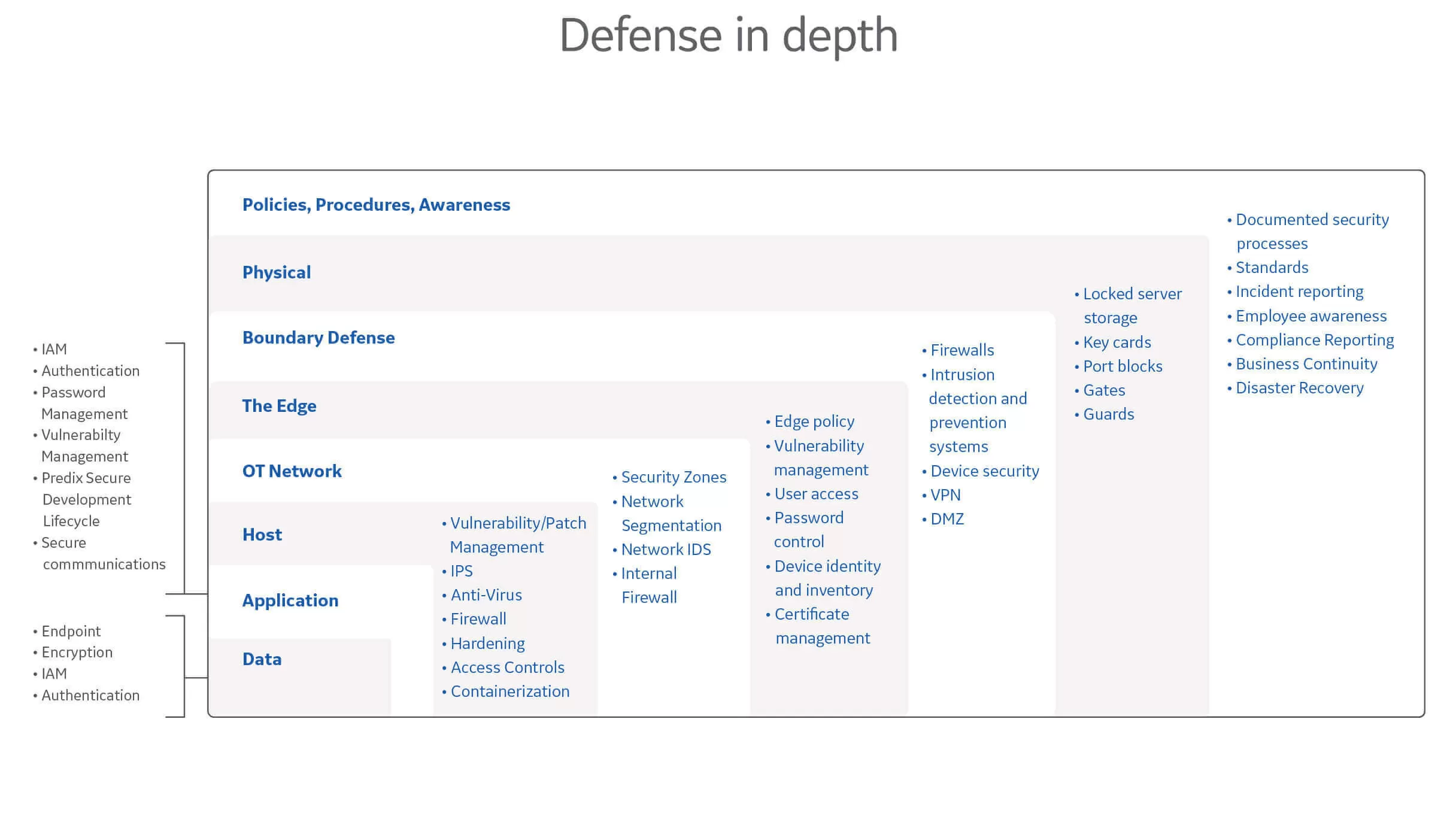
Products and services to help you ensure your own OT network security
Security and compliance at every level

Governance, compliance, and certification
GE Digital's (GED) holistic approach comprises international standards, security controls from vertical markets, and regional variations. GED helps to ensure that an organization’s fine grained controls (specific to geography or industry) are in place, validated, and audit-ready. This removes the cost for an organization to design and build their own security controls. GE Digital's cloud-hosted and software solutions are built on a common infrastructure governance model based on ISO 27001.
Secure platform and applications
The Secure Development Lifecycle (SDLC) framework includes tools, security-related guidelines, and processes that help secure the platform and all applications during the development process.
DOWNLOAD INFORMATION SECURITY & COMPLIANCE

Penetration Testing
GE’s platform and applications undergo ongoing penetration testing to identify areas where business risk may exist. Considering attack vectors, a highly specialized team of researchers carries out test scenarios and a process is in place to address any findings.
Continuous monitoring and incident response
The GE Digital cloud-hosted environment is continuously monitored by security analysts for anomalies and suspicious events that may require incident response. GE Digital’s Incident Response Program, includes on-going training, table-top exercises, pen testing, vulnerability management, and threat intelligence. Predix incident responders handle end-to-end coordination with stakeholders for swift deterministic notification, investigation, forensics, and close-out.

